Senior Writer: Paras Kela
Voice over Internet Protocol (VoIP) has emerged as a popular and cost-effective communication solution, replacing traditional phone systems. However, with the convenience and flexibility offered by VoIP, it is crucial to address the security concerns associated with this technology.
In fact, the average cost of a data breach in the US is $8.64 million. This can lead to loss of customer trust, inaccurate databases, and fragmented processes.
In this blog, we will delve into the importance of VoIP security and explore how it compares to traditional phone systems in terms of security measures. We will discuss the significance of VoIP encryption and its role in protecting sensitive voice communications from unauthorized access.
What is VoIP Security & Why is It Important?
VoIP security refers to the measures and protocols implemented to safeguard Voice over Internet Protocol (VoIP) systems and communications from various security threats. VoIP technology allows voice communications to be transmitted over the internet instead of traditional telephone lines, offering numerous advantages such as cost savings and increased flexibility. However, it also introduces unique security challenges that must be addressed.

"To ensure data security of your VoIP calls, it’s crucial to implement tested and proven techniques for VoIP security. This practice can help you keep your client conversations protected and prevent any data breach. To avoid such data risk, you can also implement a secure VoIP phone system."
The importance of VoIP security stems from the need to ensure the confidentiality, integrity, and availability of voice communications. VoIP systems can be vulnerable to various threats that can compromise sensitive information and disrupt communication processes without proper security measures.
One of the primary concerns in VoIP security is eavesdropping. Since VoIP calls travel over the internet, they are susceptible to interception by unauthorized individuals. Attackers can capture and listen to conversations, potentially gathering valuable information or compromising the privacy of individuals involved in the communication.

Another significant threat is called tampering. Hackers can manipulate or modify VoIP calls, altering the content of conversations or redirecting calls to unauthorized destinations. This poses a serious risk, especially for businesses relying on VoIP for sensitive transactions or confidential discussions.
VoIP security is paramount due to the unique risks of transmitting voice communications over the internet. Protecting the confidentiality, integrity, and availability of VoIP security systems and communications is essential to prevent unauthorized access, fraud, eavesdropping, and other security breaches. Organizations can safeguard their VoIP infrastructure and ensure secure and reliable voice communications by implementing robust security measures and promoting user awareness.
Comparing VoIP Vs Traditional Phone System Security
When comparing VoIP (Voice over Internet Protocol) and traditional phone system security, several differences and considerations come into play.
| Features | VoIP | Traditional Phone System |
|---|---|---|
| Infrastructure | Relies on internet infrastructure | Relies on physical infrastructure (copper wires, telephone lines) |
| Encryption | Requires specific VoIP security protocols and mechanisms (e.g., SRTP) for effective encryption | Encryption is generally simpler and less complex |
| Authentication | Relies on usernames, passwords, or digital credentials for user authentication | Relies on physical access control (e.g., locked cabinets, restricted areas) |
| Vulnerabilities | Susceptible to various cyber threats (e.g., DoS attacks, call interception, toll fraud, malware/phishing) | Generally less prone to digital threats, although physical security risks may still exist |
| Network Security | Depends on the security of the underlying network infrastructure (routers, switches, firewalls) | Often has dedicated and separate network infrastructure, reducing the network-based attack surface |
| Patching and Updates | Updating and patching can be more complex due to the variety of hardware, software, and protocols involved. | Updating and patching is generally more straightforward |
| User Awareness | User awareness of security best practices (e.g., strong passwords, phishing awareness) is crucial | User awareness of physical security and adherence to access control measures is important |
1. Infrastructure
Traditional phone systems rely on physical infrastructure, such as copper wires and dedicated telephone lines, which are typically more secure against external threats. In contrast, VoIP systems transmit voice calls over the internet, making them vulnerable to cyber threats unless appropriate security measures are implemented.
2. Encryption
Encryption is essential for securing both VoIP and traditional phone system communications. However, implementing encryption in VoIP systems is typically more complex due to the nature of transmitting data packets over the Internet. VoIP systems require specific protocols and mechanisms, such as Secure Real-Time Transport Protocol (SRTP), to encrypt voice traffic effectively.
3. Authentication
Both VoIP and traditional phone systems can benefit from authentication mechanisms. Traditional phone systems often rely on physical access control, such as locked cabinets or restricted areas. In contrast, VoIP systems require user authentication through usernames, passwords, or other digital credentials to ensure authorized access. However, the security of authentication mechanisms in VoIP systems heavily depends on the implementation and strength of passwords or other authentication factors.
4. Vulnerabilities
VoIP systems are exposed to unique vulnerabilities not present in traditional phone systems. For example, VoIP systems can be susceptible to Denial-of-Service (DoS) attacks, call interception, tampering, toll fraud, and malware/phishing attacks. Traditional phone systems, on the other hand, are generally less prone to such digital threats, although they may still face physical security risks.
5. Network Security
VoIP systems rely on the underlying network infrastructure, such as routers, switches, and firewalls. Therefore, ensuring the entire network’s security is crucial to protect VoIP communications. On the other hand, traditional phone systems often have dedicated and separate network infrastructure, making them less susceptible to network-based attacks.
6. Patching and updates
VoIP and traditional phone systems require regular maintenance, updates, and security patches. However, updating and patching VoIP systems can be more challenging due to the variety of hardware, software, and protocols involved. Timely application of security patches is crucial to mitigate vulnerabilities and protect against potential exploits.
7. User awareness
User awareness is essential for both VoIP and traditional phone system security. Educating users about security best practices, such as using strong passwords, being cautious of phishing attempts, and reporting suspicious activities, helps maintain the system’s overall security posture.
What Exactly is VoIP Encryption? How Does It Work?
VoIP encryption refers to the process of securing Voice over Internet Protocol (VoIP) communications by encoding voice data to prevent unauthorized access, interception, and eavesdropping. It ensures that conversations transmitted over the internet remain confidential and protected from potential threats.

The encryption process in VoIP involves transforming the voice data into an unreadable format using cryptographic algorithms. This encrypted data is then transmitted over the network and decrypted at the receiving end, allowing the intended recipient to hear the conversation in its original form. Encryption provides end-to-end security, ensuring that only authorized parties can access and understand the voice data.
Here’s a simplified overview of how VoIP encryption works:
1. Voice encoding
Voice data must first be encoded into digital packets before encryption can take place. The voice signal is divided into smaller data packets for internet transmission in this procedure. The voice data is included in these packets together with extra data like source and destination addresses.
2. Algorithms for encryption
Cryptographic algorithms are used to encrypt the voice packets. Advanced Encryption Standard (AES), Secure Real-Time Transport Protocol (SRTP), and Transport Layer Security (TLS) are common encryption techniques used in VoIP. These algorithms scramble The voice data using intricate mathematical procedures, rendering it unintelligible to those lacking the encryption key.
3. Encryption keys
An essential part of the encryption process are encryption keys. The voice data is encrypted and decrypted using them. A lengthy string of characters known as the encryption key serves as a conversation’s unique identification. To protect the privacy of the communication, the key must be generated, transferred, and managed securely by the people involved in communication.
4. Transmission
After being encrypted, voice packets are sent across the network. The scrambled voice data, source and destination addresses, and any required protocol headers are all included in the encrypted packets.
5. Decryption
The encrypted voice packets are received and processed at the receiving end. In order to reverse the encryption and restore the data to its original state, the right encryption key must be used during the decryption procedure. A decoder then turns the decrypted voice data into an audible voice signal.
Top VoIP Security Threats
VoIP (Voice over Internet Protocol) technology has revolutionized how we communicate, offering cost-effective and flexible voice communication over the Internet.
However, adopting VoIP systems also brings various security threats that organizations and individuals must be aware of and address to protect their communication networks. Here are some of the top VoIP security threats.
1. Eavesdropping
VoIP calls travel over the internet as packets of data, making them susceptible to eavesdropping. Attackers can intercept and listen to conversations, potentially gaining access to sensitive information. Eavesdropping can be particularly damaging in industries such as finance or healthcare, where confidential and personal data are frequently exchanged.
2. Call interception and tampering
Attackers can intercept VoIP calls and tamper with the content. They may alter the conversation, inject malicious content, or redirect calls to unauthorized destinations. Call tampering can lead to misinformation, fraud, and disruption of communication, compromising business operations and relationships.
3. Denial-of-Service (DoS) attacks
DoS attacks aim to disrupt or disable a VoIP system by overwhelming it with excessive traffic or resource exhaustion. Attackers flood the network or specific components of the VoIP infrastructure, causing legitimate users to be unable to make or receive calls.

DoS attacks can result in financial losses, operational disruptions, and damage to the reputation of the affected organization.
4. Toll fraud
Toll fraud occurs when unauthorized individuals gain access to VoIP systems and make unauthorized long-distance calls at the expense of the victim. Attackers exploit vulnerabilities in VoIP systems to gain control and make fraudulent calls, leading to substantial financial losses for businesses. Toll fraud is a significant concern, especially for organizations with large-scale VoIP deployments.
5. Malware and phishing attacks
VoIP systems can be targeted by malware and phishing attacks. Malicious software specifically designed for VoIP can exploit vulnerabilities and compromise the security of the system. Phishing attacks can trick users into revealing sensitive information, such as login credentials, which can be used to gain unauthorized access to the VoIP system or launch further attacks.
6. Caller ID spoofing
Caller ID spoofing involves manipulating the Caller ID information displayed on the recipient’s phone, making it appear as if the call is originating from a different number or entity.
Attackers can use caller ID spoofing to deceive users, gain their trust, or conduct social engineering attacks.
7. Insider threats
Insider threats refer to security risks posed by individuals within an organization who have authorized access to the VoIP system. Malicious insiders can exploit their privileges to eavesdrop on conversations, tamper with calls, or misuse VoIP resources for personal gain. Proper access controls, monitoring, and employee awareness programs are crucial to mitigating insider threats.
8. Weak authentication
Weak authentication mechanisms can leave VoIP systems vulnerable to unauthorized access and compromise. If weak passwords or authentication protocols are used, attackers can easily guess or crack them, gaining unauthorized access to the system. Strong and unique passwords, two-factor authentication, and regular password updates can help mitigate this threat.
9. Insider misuse
Apart from intentional insider threats, unintentional misuse by employees can also pose security risks. Lack of awareness or adherence to security policies and practices can lead to unintentional disclosure of sensitive information or accidental changes in system configurations, exposing the VoIP system to potential threats.
10. Emergency call limitations
VoIP systems may have limitations regarding emergency calls (911 services). Due to the nature of VoIP calls, emergency services may not be able to accurately determine the caller’s location, potentially delaying response times in critical situations. It is essential to understand and address these limitations to ensure the safety and well-being of users.
7 VoIP Security Best Practices to Implement
Securing your VoIP (Voice over Internet Protocol) system is crucial to protect sensitive information, ensure the privacy of communications, and prevent unauthorized access. If you’re still wondering how to secure VoIP, Here are seven best practices to enhance your VoIP security.
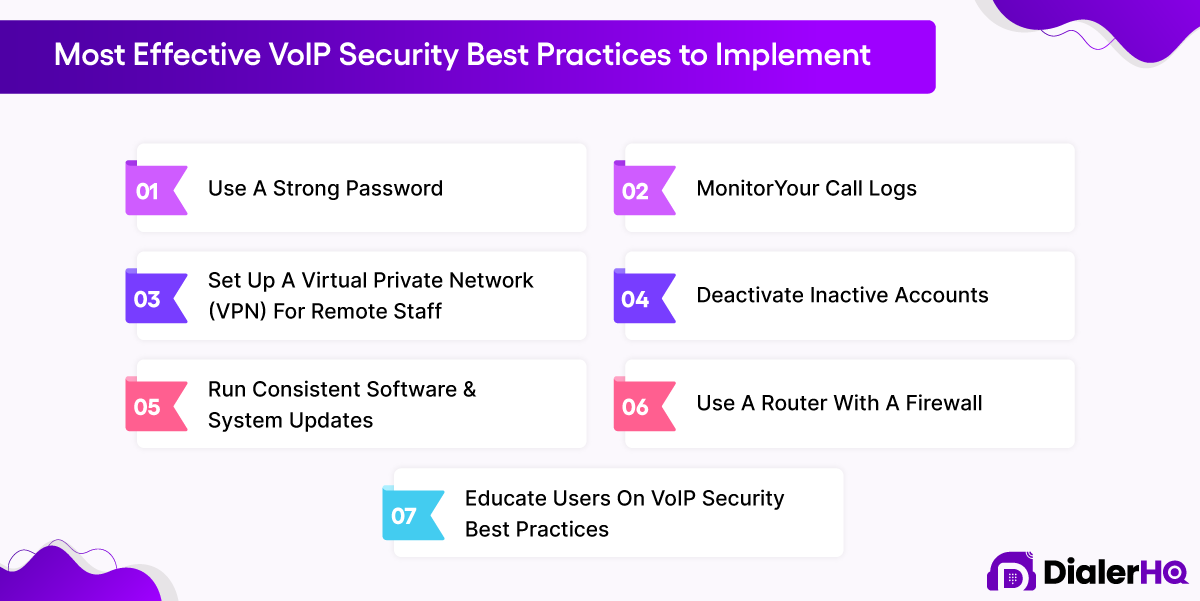
1. Use a strong password
Implementing strong passwords is essential to prevent unauthorized access to your VoIP system. Use complex, unique passwords that combine uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information like birthdays or common words. Regularly change passwords and discourage password sharing among users.
2. Monitor your call logs
Regularly review call logs and analyze any suspicious activity. Monitor for unusual call patterns, such as multiple failed login attempts or unusual call destinations. Promptly investigate any anomalies or discrepancies and take appropriate action to mitigate potential security risks.
3. Set up a Virtual Private Network (VPN) for remote staff
If you have remote workers accessing your VoIP system, consider setting up a Virtual Private Network (VPN). A VPN creates an encrypted tunnel between the remote user’s device and your network, ensuring secure communication and protecting against eavesdropping or interception of VoIP calls.
4. Deactivate inactive accounts
Regularly review and deactivate accounts of employees or users who no longer require access to the VoIP system. Inactive accounts can be targets for unauthorized access if not properly managed. Implement a process to promptly deactivate accounts when employees leave or change roles.
5. Run consistent software and system updates
Keep your VoIP system up to date by applying software updates and patches provided by the vendor. Updates often address security vulnerabilities and provide bug fixes. Regularly check for updates and apply them promptly to ensure your system is protected against emerging threats.
6. Use a router with a firewall
A firewall is a crucial component of network security. Use a router with a built-in firewall or implement a separate firewall device to protect your VoIP system. Configure the firewall to allow only authorized traffic and block potential threats from entering your network.
7. Educate users on VoIP security best practices
User awareness and training are essential to ensure a strong security posture for your VoIP system. Educate your users on security best practices, such as recognizing phishing attempts, avoiding clicking on suspicious links or downloading unknown attachments, and reporting any suspicious activities. Regularly reinforce security awareness through training sessions or informational materials.
How to Choose a Secure VoIP Provider?
Choosing a secure VoIP (Voice over Internet Protocol) provider is essential to ensure your communication network’s confidentiality, integrity, and availability. Here are some key factors to consider when selecting a secure VoIP provider.

1. Encryption
Inquire about the encryption protocols and mechanisms the provider uses to secure voice communications. Look for providers that offer strong encryption, such as Secure Real-Time Transport Protocol (SRTP) or Transport Layer Security (TLS), to protect your calls from interception and eavesdropping.
2. Network security
Assess the provider’s network security measures. They should have robust firewalls, intrusion detection and prevention systems, and other security controls in place to safeguard against network-based attacks. Additionally, they should have measures to protect against distributed denial-of-service (DDoS) attacks.
3. Privacy policy
Review the provider’s privacy policy to understand how they handle and protect your data. Ensure that they adhere to industry-standard data protection practices and comply with relevant privacy regulations. Look for providers that offer end-to-end encryption and have strict access controls to protect your data from unauthorized access.
4. Authentication and access controls
Inquire about the provider’s authentication mechanisms for user access. They should have strong authentication measures, such as two-factor authentication or multi-factor authentication, to ensure only authorized users can access the system. Additionally, they should have robust access controls to limit privileges and prevent unauthorized changes or misuse of the VoIP system.
5. Secure infrastructure
Assess the provider’s infrastructure security. They should have redundant systems, backup and disaster recovery measures, and physical security controls to protect against outages, data loss, and unauthorized physical access to their facilities. A secure infrastructure ensures the availability and reliability of your VoIP services.
6. Compliance and certifications
Check if the provider adheres to industry standards and has relevant certifications for data security and privacy, such as ISO 27001 or SOC 2. Compliance with these standards demonstrates their commitment to maintaining a secure environment for your VoIP communications.
Comparison of Top 5 Most Secure VoIP Providers
| Brand Name | Key Features | Pricing | Free Trial |
|---|---|---|---|
| DialerHQ |
|
| 10 Days |
| Callhippo |
|
| 10 Days |
| RingCentral |
|
| 14 Days |
| Nextiva |
|
| 10 Days |
| 8x8 |
|
| 30 Days |
Top 5 Most Secure VoIP Providers
While it’s important to conduct thorough research and consider specific requirements when choosing a secure VoIP provider, here are five reputable VoIP providers known for their commitment to security.
1. DialerHQ
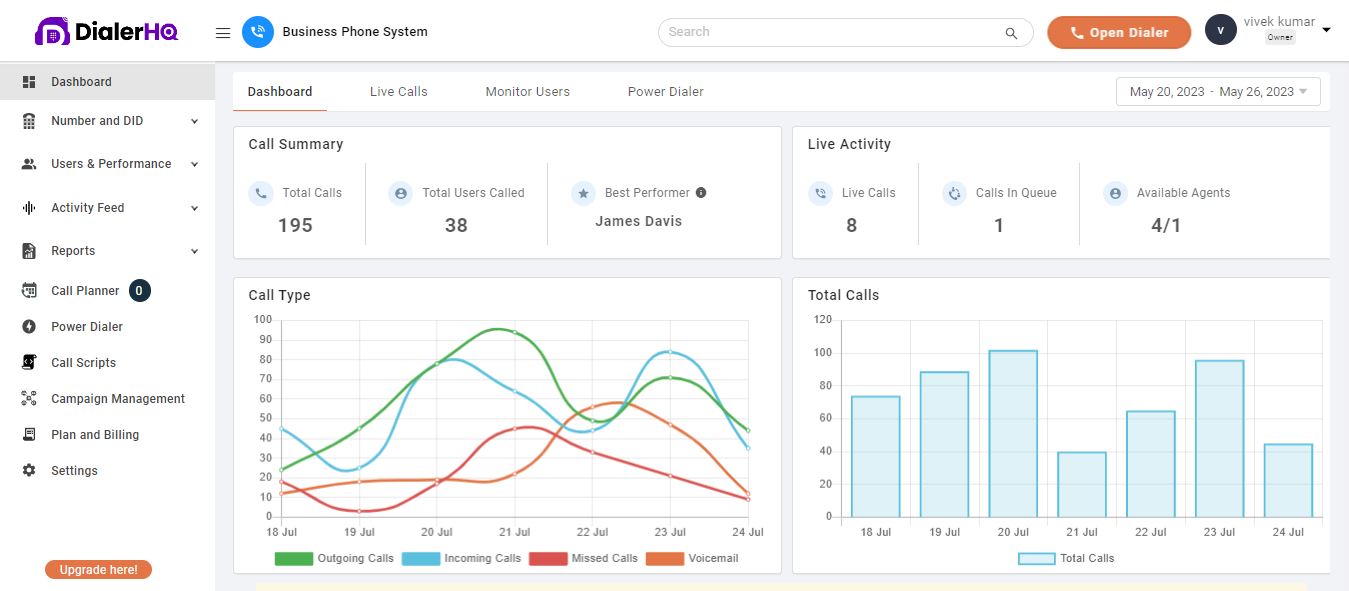
DialerHQ is a cloud-based VoIP provider focused on call center solutions. It offers a feature-rich dialer platform that enables businesses to efficiently manage outbound calls, track performance metrics, and improve customer engagement. This is one of the most secure VoIP providers you can get in the market.
Features
- Secure call routing
- Call recording
- Real-time monitoring
- Agent authentication
- Call forwarding
- International VoIP system
Pros and Cons
- Strong encryption algorithms protect voice calls from unauthorized access.
- Secure transmission protocols ensure safe data transfer.
- Provides features for call recording encryption and user authentication.
- Limited availability of certain advanced features compared to other platforms.
- Integration options with other business tools may be limited.
Pricing
As an enterprise-specific solution, DialerHQ caters exclusively to large teams or organizations. Connect with the DialerHQ sales team at [email protected] for personalized quotes, or start a free trial for first-hand experience.
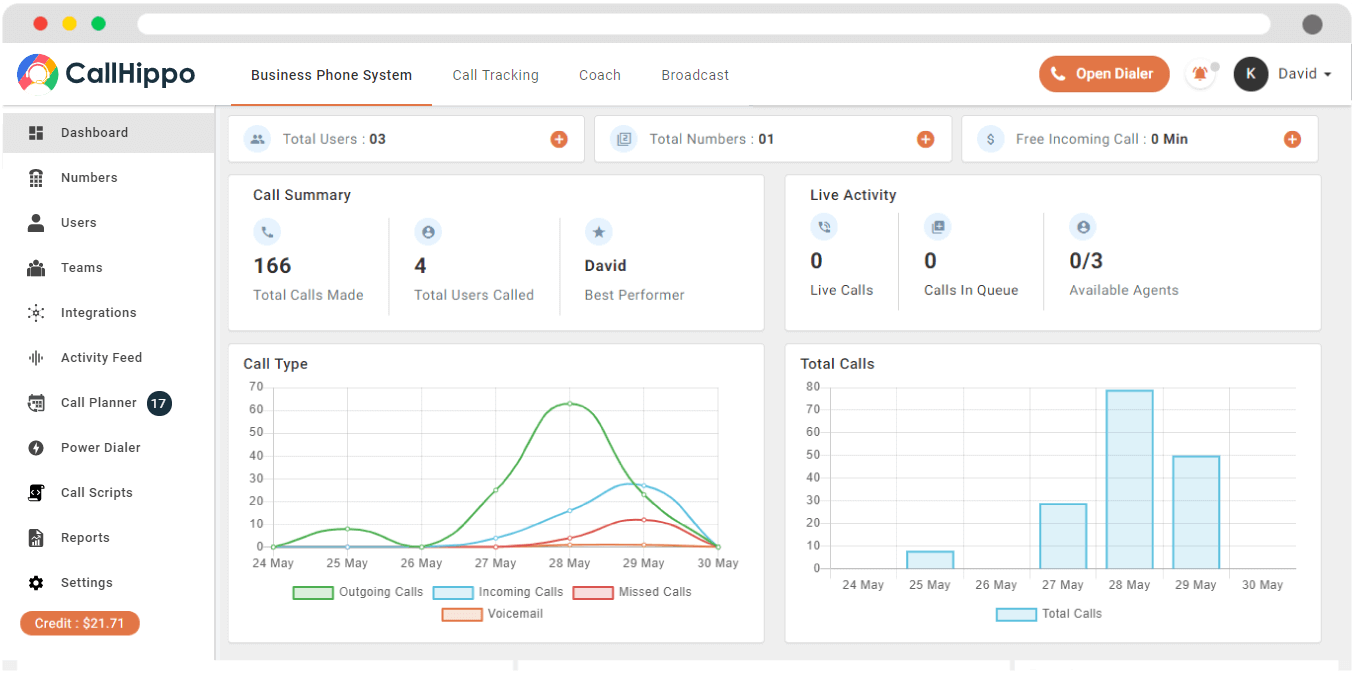
2. CallHippo
CallHippo is a secure VoIP provider that offers encrypted and reliable communication solutions. It utilizes encryption protocols to protect voice calls from unauthorized access and maintains the privacy of conversations.
CallHippo implements security measures to prevent phone calls tampering, call hijacking, and eavesdropping, ensuring secure communication channels. Additionally, this VoIP secure platform provides features like two-factor authentication and secure call recordings to enhance the overall security of its VoIP services. CallHippo is one of the best VoIP phone systems that offer advanced features and provides excellent customer support.
Features
- Encrypted voice calls
- Eavesdropping prevention
- Two-factor authentication
- Secure call recordings
- Protection against call tampering
Pros and Cons
- Encryption protocols ensure secure voice calls and protect sensitive conversations.
- Provides secure call recordings and two-factor authentication.
- Offers measures to prevent call tampering and eavesdropping.
- Integration options with certain business applications may be limited.
- Advanced features may only be available in higher-tier plans.
Pricing plans
- Basic – $0
- Bronze – $16
- Silver – $24
- Platinum – $40
3. RingCentral
RingCentral is a leading cloud communications and collaboration platform that provides VoIP services to businesses of all sizes. It offers a comprehensive suite of communication tools, including voice, video, messaging, and conferencing, designed to enhance productivity and streamline communication workflows.
Features
- Secure file sharing
- 2-Factor authentication
- Secure call recording
- Advanced reports and analytics
- Security compliant
Pros and Cons
- Advanced encryption ensures secure and private voice calls.
- Robust compliance features meet stringent security requirements.
- Reliable and encrypted communication services.
- Some users may find RingCentral's pricing to be on the higher side.
- Customer support response times may vary.
Pricing
- Core – $20 per user per month.
- Advanced – $25 per user per month.
- Ultra – $35 per user per month.
4. Nextiva
Nextiva is a trusted and secure VoIP provider that focuses on delivering secure communication solutions to businesses. It employs industry-standard encryption techniques to protect voice calls and ensures secure data transmission over the internet.
Nextiva also provides advanced security features, such as secure voice conferencing and encrypted call recordings, to maintain the confidentiality and integrity of communications. With Nextiva, businesses can enjoy high security and peace of mind when using VoIP services.
Features
- Secure data transmission
- Encrypted call recording
- Security and compliance
- Call forwarding
- Secure call recording
- Secure voice conferencing
Pros and Cons
- Utilizes industry-standard encryption techniques for secure voice calls.
- Offers secure voice conferencing and encrypted call recordings.
- Provides compliance and security features to meet industry regulations.
- Some users may find the interface and user experience to be less intuitive.
- Advanced features may require additional costs or higher-tier plans.
Pricing
- Essential – $18.95 per user per month.
- Professional – $22.96 per user per month.
- Enterprise – $32.95 per user per month.
5. 8×8
8×8 is a highly secure VoIP provider that prioritizes the protection of user communications. It employs strong encryption algorithms and secure transmission protocols to safeguard voice calls from potential threats.
8×8 offers advanced security features, such as encrypted voice traffic, secure call recording, and multi-factor authentication, to ensure the confidentiality and integrity of communications. With its robust security measures, 8×8 provides a secure and reliable VoIP solution for businesses and individuals.
Features
- Secure recording
- Multi-factor authentication
- Encrypted voice traffic
- Secure and compliant features
- Call forwarding
- Voice conferencing
Pros and Cons
- Strong encryption algorithms protect voice calls and ensure communication privacy.
- Offers secure call recording and multi-factor authentication.
- Provides comprehensive compliance and security features.
- Some users may find the user interface to be less user-friendly.
- Advanced features may require additional configuration and setup.
Pricing
- X2 – $24 per user per month.
- X4 – $44 per user per month.
Conclusion
The importance of VoIP security cannot be overstated in today’s interconnected world. With their strong encryption algorithms, secure call recording, and multi-factor authentication, the featured VoIP providers provide robust protection for voice calls and ensure communication privacy. Their comprehensive compliance and security features further enhance the overall security posture.
While some users may find the user interface less user-friendly and advanced features may require additional configuration, the benefits of the secure communication solutions these providers offer outweigh these minor drawbacks. Investing in a reliable and secure VoIP provider is crucial for businesses and individuals seeking to safeguard their sensitive conversations and maintain the confidentiality of their communications.
FAQs
VoIP is not immune to hacking, but implementing strong security measures such as encryption, authentication, and secure transmission protocols can greatly enhance the safety of VoIP communications.
VoIP is vulnerable to attacks such as eavesdropping, call interception, call hijacking, identity spoofing, and denial-of-service (DoS) attacks. Implementing security measures can help mitigate these VoIP security risks and provide VoIP users with a safe platform.
Yes, using a Virtual Private Network (VPN) can provide an additional layer of security for VoIP calls. A VPN encrypts the traffic between the user's device and the VoIP server, making it difficult for hackers to intercept or eavesdrop on the calls.
Encryption technology, such as Secure Real-time Transport Protocol (SRTP), is commonly used to protect VoIP against eavesdropping. SRTP encrypts the voice packets during transmission, ensuring that only authorized parties can access the conversation.
The Secure Real-time Transport Protocol (SRTP) is a commonly used protocol that protects VoIP. SRTP provides encryption, authentication, and integrity checks to secure the voice data transmitted over the network. Other protocols such as Transport Layer Security (TLS) and Secure Socket Layer (SSL) can also be used to protect signaling and control messages in VoIP systems.

Paras Kela is an accomplished IT professional with 7+ years of industry experience, including 4+ years as a dedicated content writer. His expertise lies in crafting informative blogs on VoIP and cloud telephony, among other technical subjects. Outside his professional pursuits, he cherishes quality time with loved ones, indulges in watching documentaries, and finds solace in gardening.
Updated : April 10, 2024

Subscribe to our newsletter & never miss our latest news and promotions.